How To Create an Effective Ecommerce Return Policy and Process
Conduct research on your competitors to see what types of terms they include in their return…

Conduct research on your competitors to see what types of terms they include in their return…

What are the best WordPress Security plugins and how to set them up the best way…

The Most Important Stages and Plugins for WordPress Website Development Developing a WordPress website requires careful…
Powerful SEO Tools for WordPress Search Engine Optimisation (SEO) is essential for improving your WordPress website’s…
“The comprehensive coverage of the SaaS ecosystem fueled by solid threat prevention, detection, and response capabilities…
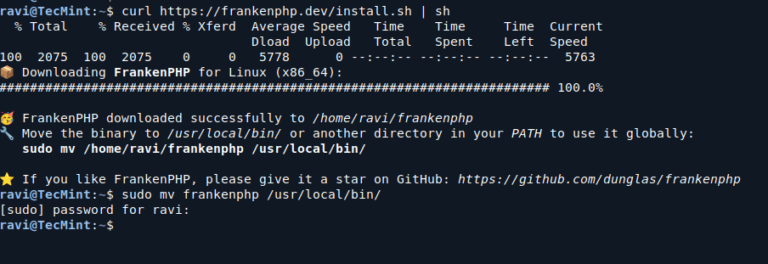
FrankenPHP is a modern application server for PHP that enhances the performance and capabilities of PHP…

Trust icons quickly communicate key value propositions and benefits in a visual way, allowing the user…

In the competitive landscape of e-commerce hosting, leveraging the right tools can be a game changer…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
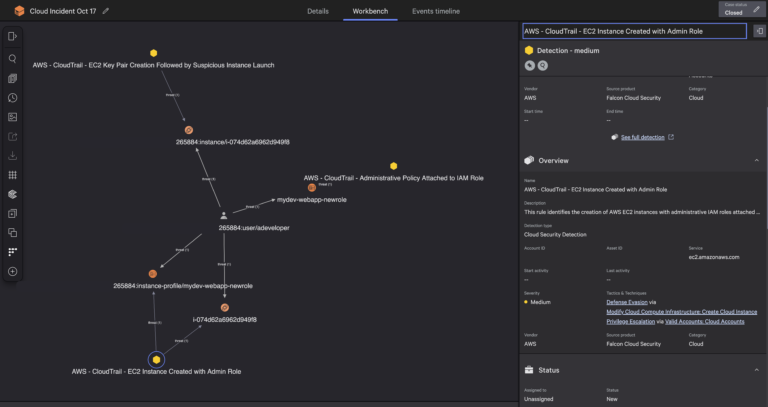
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
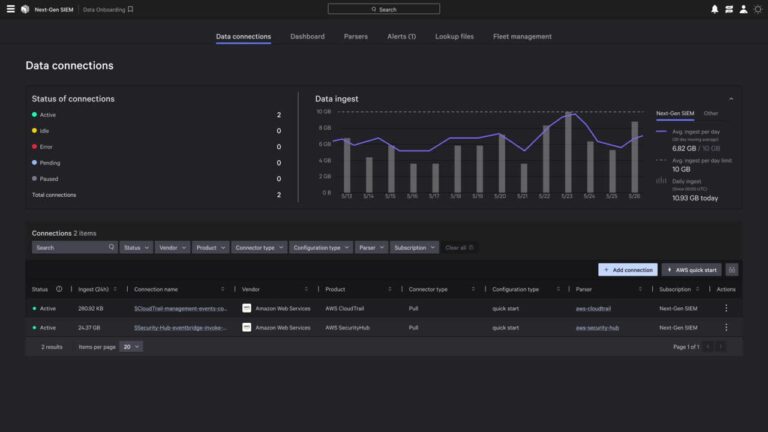
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
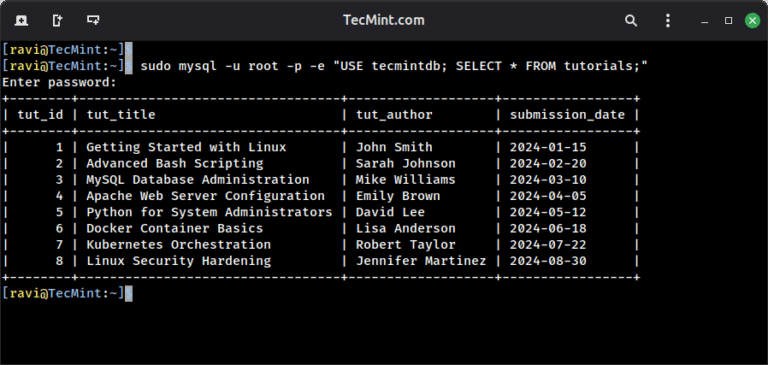
If you are in charge of managing a database server, from time to time you may…
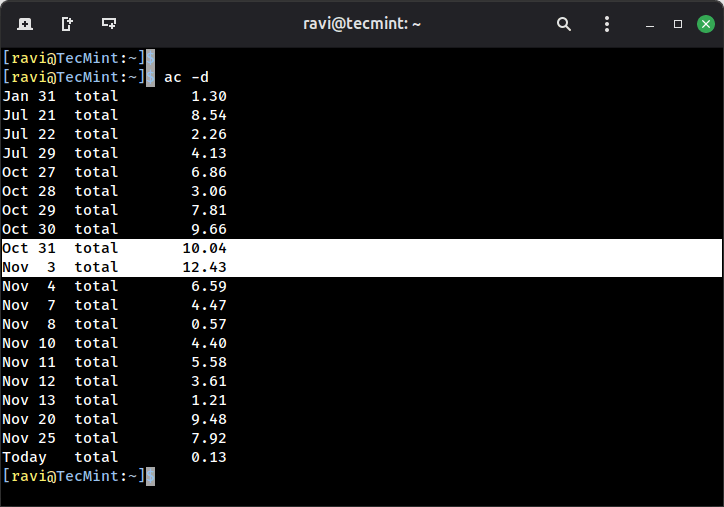
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
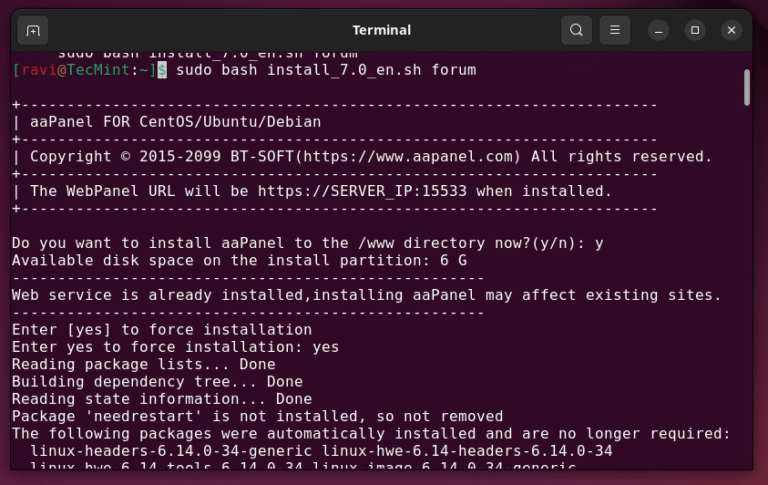
Managing a web server through command-line alone can feel like you’re juggling too many things at…
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….

Apple iWork is Apple’s suite of office applications, similar to Microsoft Office or Google Docs, consisting…
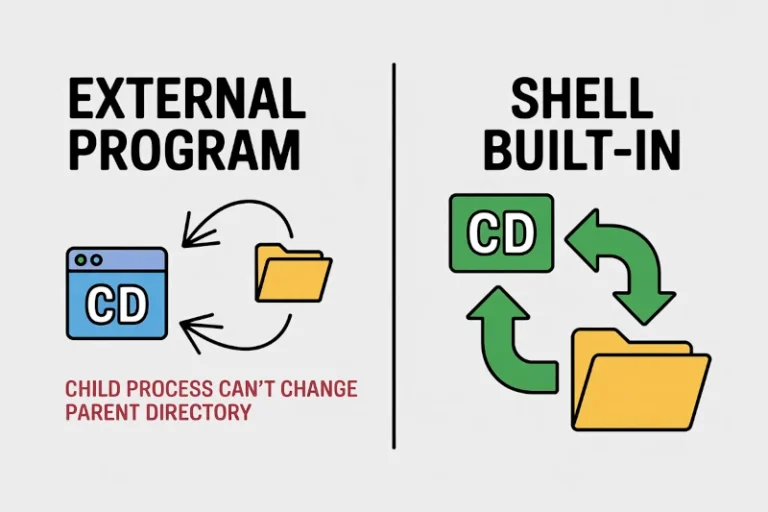
In Linux, the ‘cd‘ (Change Directory) command serves as a fundamental navigation tool for both newcomers…
Here, we examine a case study in which CrowdStrike OverWatch threat hunters identified and disrupted BLOCKADE…